I recently completed a network implementation for a client, of which a component was the deployment of multiple Azure firewall rules and IP Groups via ARM templates.
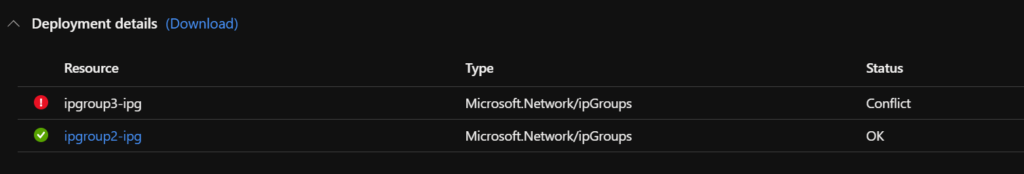
Deploying new IP Groups and rules was working without any issues but would fail when trying to update existing IP Groups with a “Status: Conflict” error such as the one below.
Deployment failure of updated IP Groups:

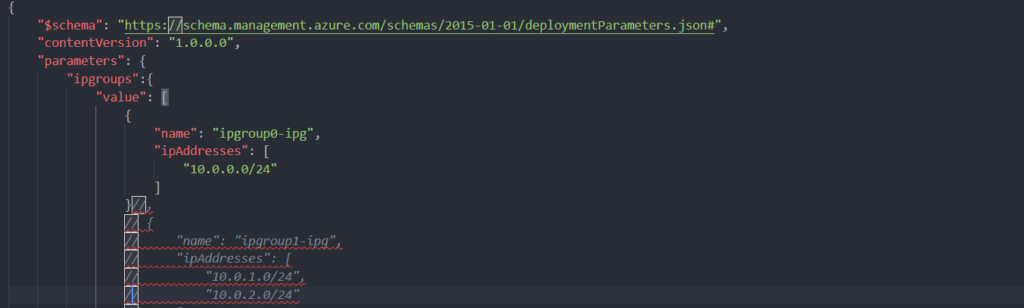
Once I saw failures, I started troubleshooting by minimizing the number of IP Groups being deployed in the ARM template, in the example below I was only updating a single IP Group. This was successful. I then tested using Azure firewall PowerShell modules to update single rules one after the other – both of which worked.
Minimized parameter file:
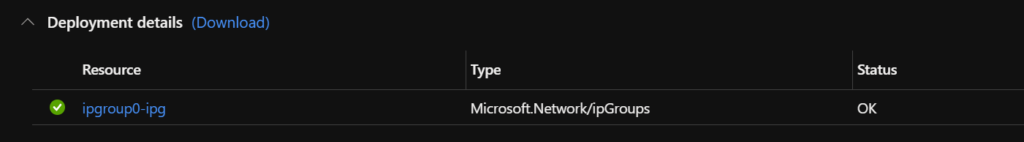
A successful single deployment:
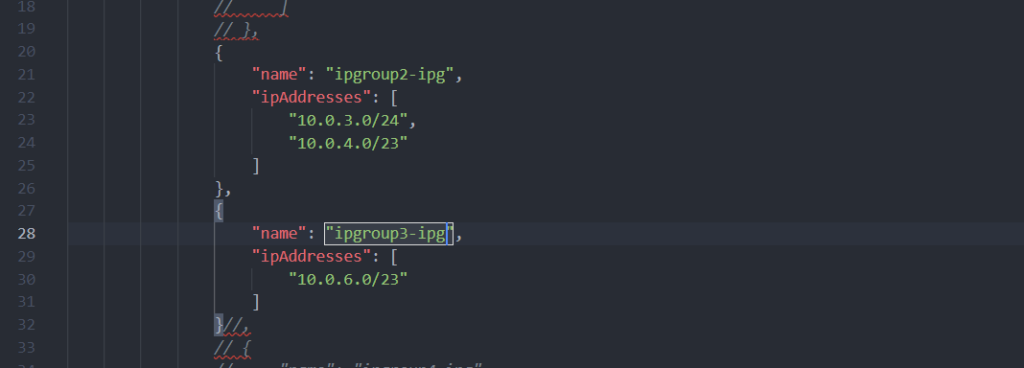
To verify that deployments with more than a single IP Group are causing the issue, I enabled two IP Groups to be updated in the parameter file below.
Enabling multiple IP Groups in the parameter file:
As the output below shows, one of the IP Groups updated successfully the other one did not.
Failure when more than a single IP Group is enabled:
Having narrowed down the issue to multiple rule updates via ARM, I started looking at how ARM was executing the rule updates.
To minimize code in ARM templates we tend to use a copy loop to iterate through arrays, which by default will be processed in parallel. The following article describes the copy loop: Deploy multiple instances of resources – Azure Resource Manager | Microsoft Docs
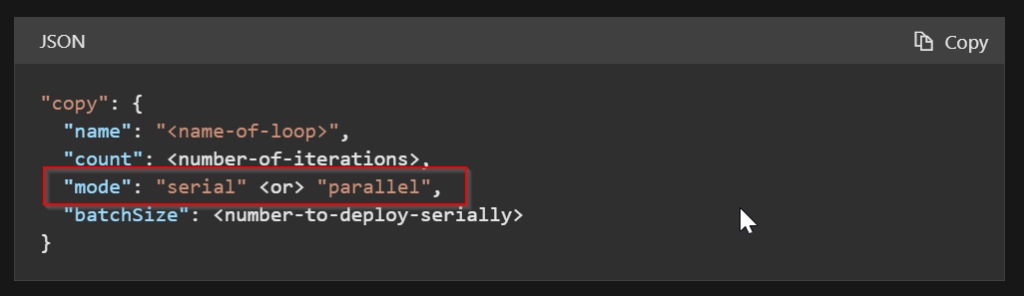
Parallel deployment is not normally an issue with ARM when creating or updating resources in Azure. However, when updating IP Groups, the deployment was failing with a conflict.
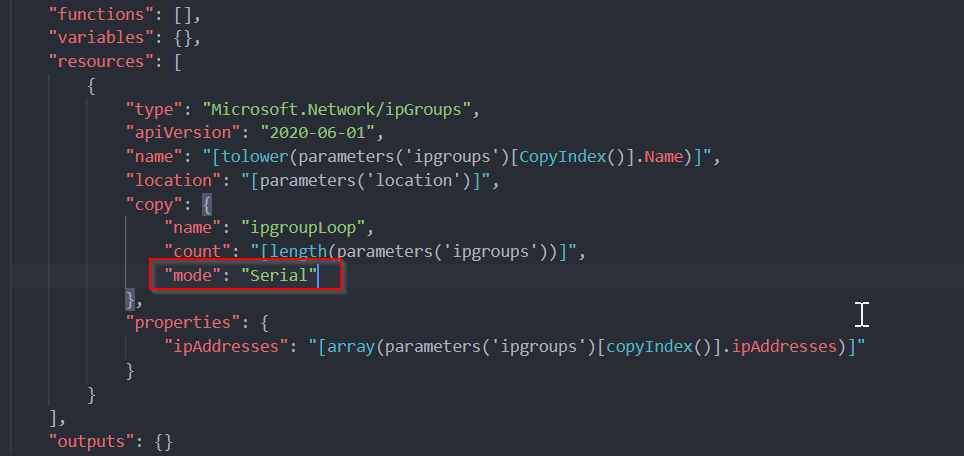
A solution that worked for me was to set the mode of the copy loop to serial. This way the elements are processed sequentially, waiting for completion of the previous element, and we don’t end up with an update conflict. In the example below I added mode with the value of Serial to the ipGroups resource.
Added “mode: Serial”:
Note: This will slow down your deployment, if you have a lot of rules and are using pipelines (such as Azure Devops) to deploy these updated IP Groups you may need to consider timeouts in your deployment pipelines.
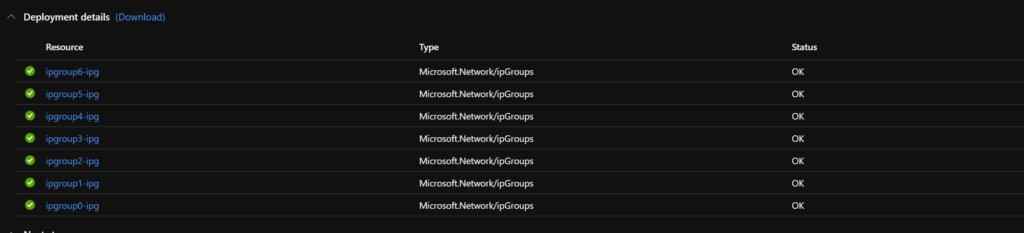
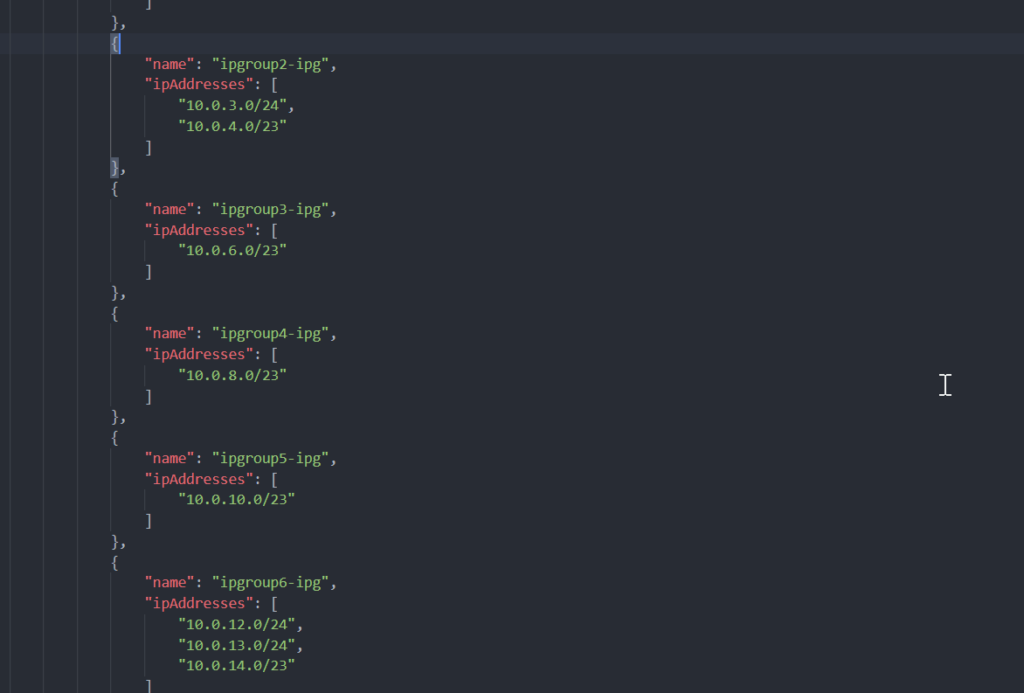
Enabled all IP Groups:
Below is the output of a successful deployment: