Given the cost of private endpoint traffic ingress/egress for data-heavy applications, we have found that opting to configure Azure Storage Firewalls and Virtual Networks provides a very cost-effective measure with similar controls to private endpoints. This post will cover the key steps needed to configure Azure Storage Firewalls and Virtual Networks.
Prerequisites
The following prerequisites must be actioned before continuing any further:
- To apply a virtual network rule to a storage account, the user must have one of the following permissions for the subnets being added:
- Storage Account Contributor
- Permission to the Microsoft.Network/virtualNetworks/subnets/joinViaServiceEndpoint/action Azure resource provider operation via a custom Azure role
- Applications that access a storage account when network rules are configured require proper authorisation
Firewall and Virtual Network Configuration
Currently, PowerShell is the only supported method for configuring virtual networks on storage accounts. The following steps need to be taken to configure Azure Storage Firewalls and Virtual Networks:
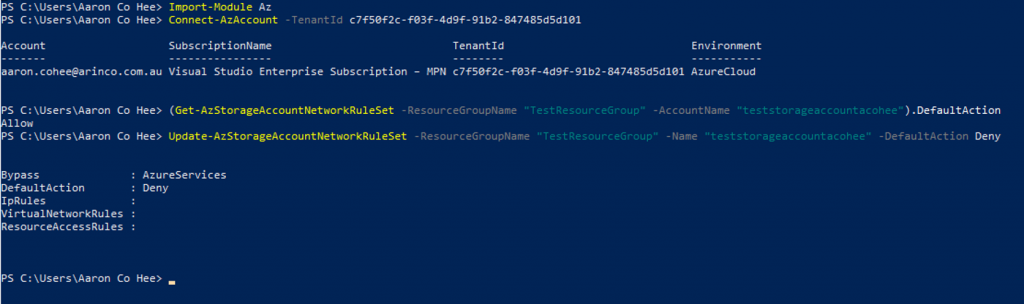
- Firstly the default network access rule needs to be changed. By default, storage accounts accept connections from clients on any network.
- Import the AzureAD Module and sign in to Azure
- Display the status of the default rule for the storage account.
(Get-AzStorageAccountNetworkRuleSet -ResourceGroupName "myresourcegroup" -AccountName "mystorageaccount").DefaultAction
- Set the default rule to deny network access by default.
Update-AzStorageAccountNetworkRuleSet -ResourceGroupName "myresourcegroup" -Name "mystorageaccount" -DefaultAction Deny
- If you want to roll back the change simply enter the PowerShell command below.
Update-AzStorageAccountNetworkRuleSet -ResourceGroupName "myresourcegroup" -Name "mystorageaccount" -DefaultAction Allow
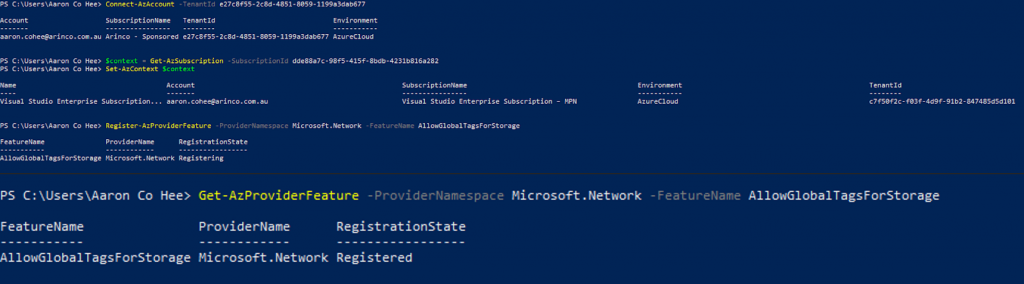
- Now if the virtual network is located in another Azure AD Tenant or in a region other than the region of the storage account or its paired region, to enable access to the storage account register the AllowGlobalTagsForStorage feature. To do this the following PowerShell commands must be run
- Sign in to your Azure subscription with the Connect-AzAccount command and follow the on-screen directions.
- If your identity is associated with more than one subscription, then set your active subscription.
$context = Get-AzSubscription -SubscriptionId <subscription-id>
Set-AzContext $context
- Register the AllowGlobalTagsForStorage feature by using the Register-AzProviderFeature command.
Register-AzProviderFeature -ProviderNamespace Microsoft.Network -FeatureName AllowGlobalTagsForStorage
- To verify that the registration is complete, use the Get-AzProviderFeature command.
Get-AzProviderFeature -ProviderNamespace Microsoft.Network -FeatureName AllowGlobalTagsForStorage
- Lastly, the virtual network rules must be configured, to do this run the following PowerShell commands
- Import the AzureAD Module and sign in to Azure
- List virtual network rules.
(Get-AzStorageAccountNetworkRuleSet -ResourceGroupName "myresourcegroup" -AccountName "mystorageaccount").VirtualNetworkRules
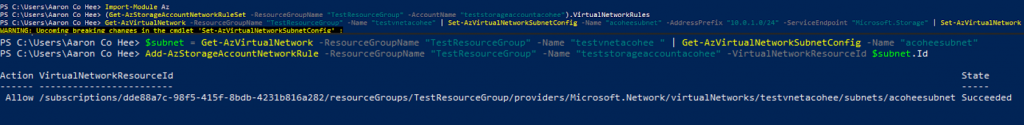
- Enable service endpoint for Azure Storage on an existing virtual network and subnet.
Get-AzVirtualNetwork -ResourceGroupName "myresourcegroup" -Name "myvnet" | Set-AzVirtualNetworkSubnetConfig -Name "mysubnet" -AddressPrefix "10.0.0.0/24" -ServiceEndpoint "Microsoft.Storage" | Set-AzVirtualNetwork
- Add a network rule for a virtual network and subnet.
$subnet = Get-AzVirtualNetwork -ResourceGroupName "myresourcegroup" -Name "myvnet" | Get-AzVirtualNetworkSubnetConfig -Name "mysubnet"
Add-AzStorageAccountNetworkRule -ResourceGroupName "myresourcegroup" -Name "mystorageaccount" -VirtualNetworkResourceId $subnet.Id
- To add a network rule for a subnet in a VNet belonging to another Azure AD tenant, use a fully-qualified VirtualNetworkResourceId parameter in the form “/subscriptions/subscription-ID/resourceGroups/resourceGroup-Name/providers/Microsoft.Network/virtualNetworks/vNet-name/subnets/subnet-name”.
- If you want to roll back this change and remove the network rule for a virtual network and subnet, Run the following PowerShell commands
$subnet = Get-AzVirtualNetwork -ResourceGroupName "myresourcegroup" -Name "myvnet" | Get-AzVirtualNetworkSubnetConfig -Name "mysubnet"
Remove-AzStorageAccountNetworkRule -ResourceGroupName "myresourcegroup" -Name "mystorageaccount" -VirtualNetworkResourceId $subnet.Id
Best Practices
To secure your storage account, it is encouraged to take the following actions:
- Configure a rule to deny access to traffic from all networks (including internet traffic) on the public endpoint, by default
- From there configure rules that grant access to traffic from specific virtual networks
This configuration enables you to build a secure network boundary for your applications. We can also combine firewall rules that allow access from specific virtual networks and from public IP address ranges on the same storage account. These storage firewall rules can be applied to existing storage accounts, or when creating new storage accounts.
Note: Classic storage accounts do not support firewalls and virtual networks
Conclusion
In this blog post, we looked at how we can configure Azure Storage Firewalls and Virtual Networks and the benefits it brings. Hopefully, you have found this post informative, if you know of another method to reduce the costs of private endpoint traffic ingress/egress let us know and don’t be afraid to share your thoughts.