Access control is important because it helps protect our spaces and information from unauthorised access, ensuring safety and security in both the physical and digital world. Imagine your home, workplace, or favourite online account without access control, anyone could walk in or log on, putting everything from personal belongings to sensitive data at risk. By setting rules about who can access certain areas or information, we can prevent breaches, protect privacy, and maintain order. In this article, we’ll explore some access control features of Entra ID that are quite easy to use but often overlooked.
Key objectives
In a nutshell, we want:
- Right person to get access to the
- Right resource
- At the right time
On-boarding use case
Consider a use case with employee on-boarding. Let’s say our new starter works in sales. At the very least they need access to: email and communication platforms, the Customer Relationship Management (CRM) System and product training portals. They might also need access to Sales Enablement Tools, Document Management Systems, Proposal and Quoting Software company’s ERP, Analytics and Reporting Tools.
Each of these items typically requires a separate request to the Service Desk, often involving approval processes and varying turnaround times. As a result, new starters often experience significant delays before they can begin working productively. This inefficiency translates to substantial financial losses for the company. On average, it can take 5 to 10 business days for a new starter to become fully operational if onboarding processes aren’t streamlined, especially in environments where multiple systems require separate access requests.
For example, if we consider a Sales Manager with a salary of $100,000, the cost of their downtime could be approximately $3,800. With a turnover rate of 10%, a company with 10,000 employees would have around 1,000 new starters each year, potentially incurring a cost of $3,800,000 annually due to onboarding inefficiencies alone.
Automating the onboarding process could lead to significant cost savings for the company. By streamlining access provisioning and reducing the need for manual service desk requests, new starters could become productive much faster. This not only minimises downtime but also reduces administrative burdens on IT staff, allowing resources to be allocated more efficiently.
Common challenges
The speed of onboarding is not the only concern – security is just as critical. Common challenges include:
- Manual Access Requests: These are often made through multiple channels, such as phone calls or emails, leading to inconsistencies and inefficiencies.
- Manual Granting of Access: The Service Desk typically adds individuals to groups manually, increasing the risk of errors and delays.
- Accumulation of Permissions: Once people are added to a group, they are rarely removed, resulting in a buildup of unnecessary permissions over their tenure.
- Inconsistent Access Control Mechanisms: Different applications use varying methods for access control, often embedded directly within the application, complicating management and auditing.
- Access Cloning: Employees frequently request to replicate a colleague’s group memberships (e.g., “Just give me the same group memberships that John has so I can do my job”), which can perpetuate inappropriate access and security risks.
Conceptual solution
But is there a solution? Or how do you even approach it?
Let’s break it down.
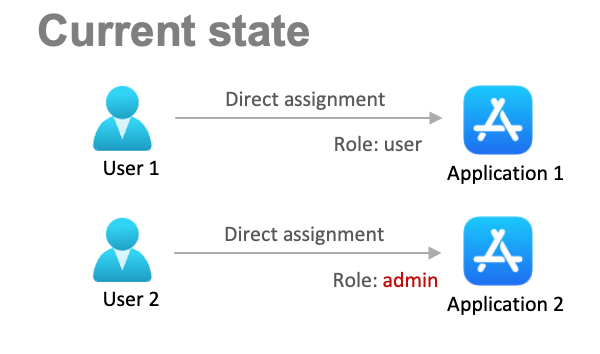
First, can we control everything via group memberships?
E.g. if user is a member of the “Application1 – core” group, they will have basic level access to the app; and if they are in the “Application1 – admins” they have admin access.
Let’s consider it our “current state”.
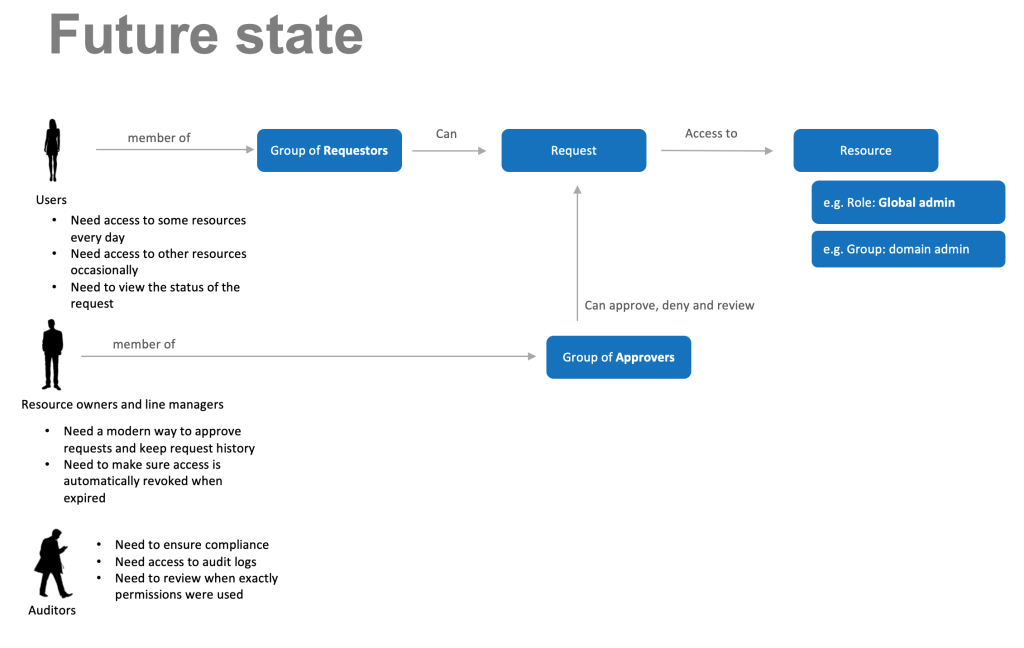
Now if we add requestors and approvers, what a conceptual version of our future state could look like?
Entra ID capabilities
Now to the best part – is there a technology that could help us to do this?
Well, there’s many, and chances are you already have it but maybe just not using it yet?
You are probably already familiar with Entra Privileged Identity Management. That works great with built it Entra ID roles for admins. But what about business users and resources?
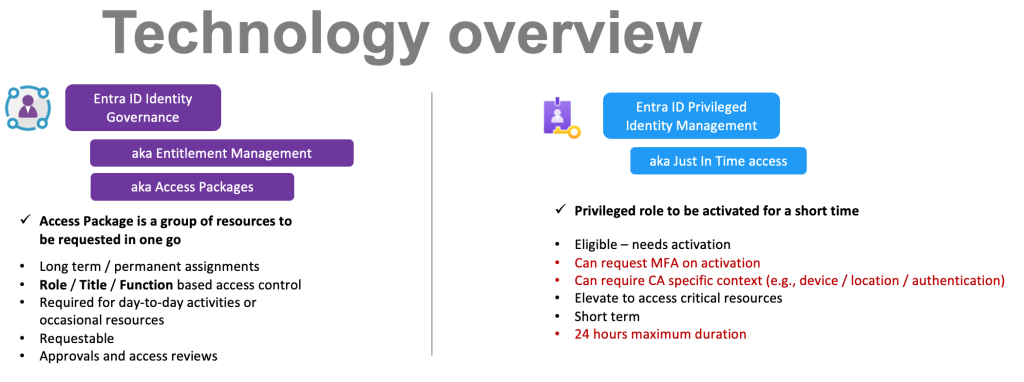
If we look at Entra ID Privileged Identity Management and Entra ID Identity Governance, we can find many similarities. In fact (if you are open to this idea), in many cases Privileged Identity Management can be even replaced by the properly constructed access packages in Identity Governance, simplifying management and improving/unifying user experience to request different resources.
Now let’s get back to our oversimplified use case and look what our future state might look like with the Identity Governance in place:
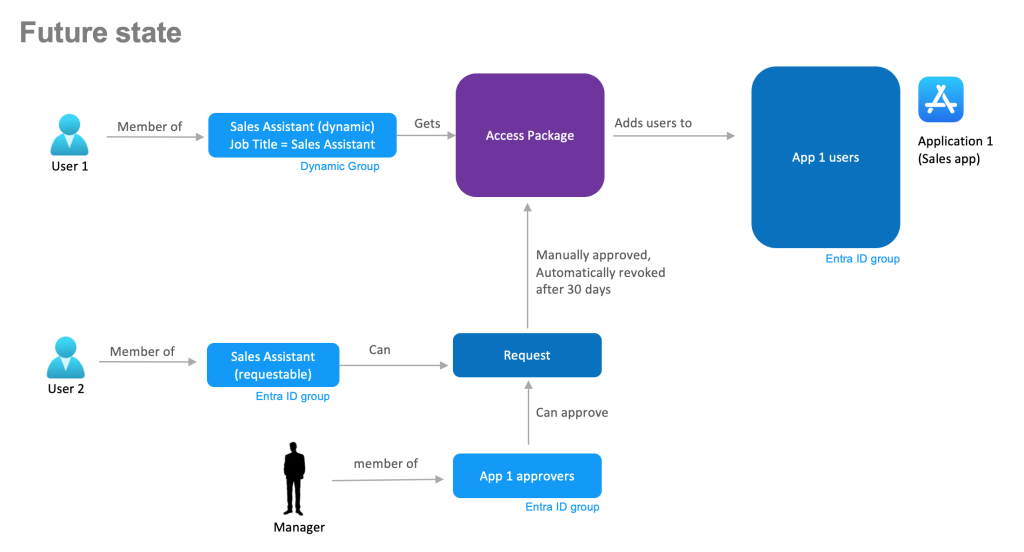
It might look simple, but ticks many boxes:
- Automatic role-based and attribute-based access control via Entra ID dynamic groups
- Access is automatically approved if user has specific attributes such as a role and/or location
- Access is automatically revoked if user attribute changes as they move in the company’s structure
- Requestable access via Identity Governance Access Packages
- Ad hoc access has a set duration and will be automatically removed
Can this be expanded to the on-premises infrastructure without a third-party solution using just OTTB Entra ID features? Yes, it can, perhaps we’ll cover it in the next post – stay tuned.
Other considerations
- Naming standards (for resources, approvers and reviewers)
- Default parameters (e.g. access duration) – keep it simple but consistent)
- Some level of flexibility (e.g. permanent access)
- Scripted deployment for a quick and consistent environment
Conclusion
Leveraging Identity Governance Access Packages and the capabilities of Entra ID offers a robust framework for managing access within the company’s structure. By adhering to best practices such as standardised naming conventions, unified default parameters, and ensuring a degree of flexibility, you can create a streamlined and secure access management environment. Scripted deployment further enhances the efficiency and consistency of the implementation, paving the way for a resilient and scalable infrastructure.
Stay tuned for our next post where we will delve deeper into extending these practices to on-premises infrastructure.







